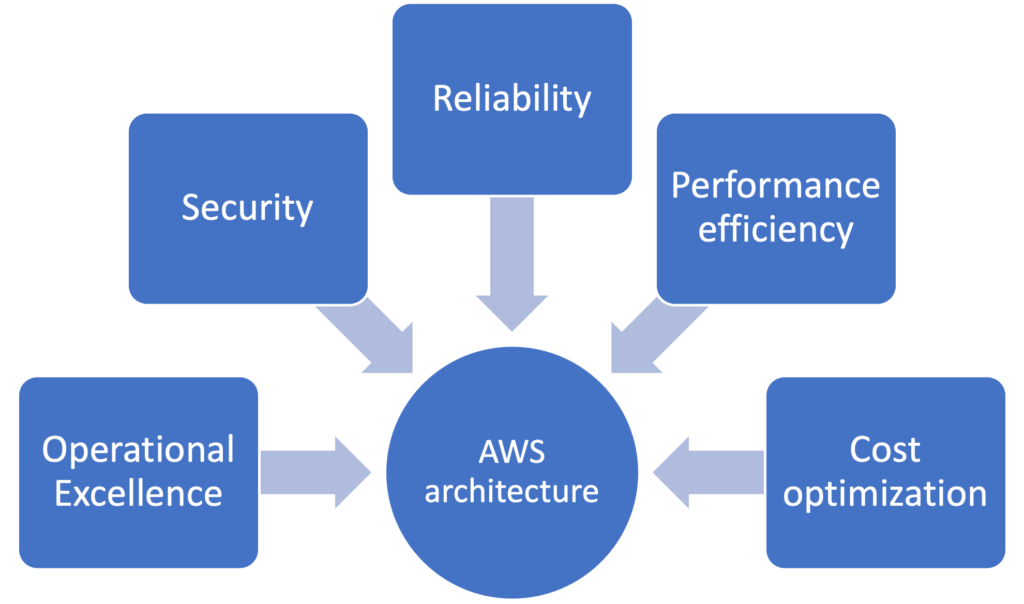
AWS has taken up the market by storm. Today, AWS accounts for 33.8% of the market share globally. No wonder, AWS is the market leader. AWS has provided a well-architecture framework. Five key pillars of the AWS framework are:
To leverage the key advantages of the robust architecture of AWS, best practices must be followed. Let us discuss some of the best practices that everyone must know.
1. Protecting AWS credentials
Your AWS account signifies a business relationship between you and AWS. You would use an AWS account to manage all AWS resources and services. For managing this, full access must be given to the account that aggravates the security risks.
One of the best practices would be to create one or more AWS Identity and Access Management (IAM) users and give them the necessary permissions to manage the daily interactions.
2. Safeguarding Applications
Access to your AWS applications to the outside world should be given when it is necessary. For making an application exclusive to a particular group (Or IPs), a security group should be created for that web server. This security group can be used to restrict based on IP & ports through which the application is accessed. Entry to your server should be forbidden for all other internet traffic.
3. Backup & Recovery
Backup and recovery are proactive measures to mitigate different issues that might occur during and after application deployment. For that case, one must be prepared with a backup plan. Some checkpoints regarding data backup and recovery are:
- Regularly backup your amazon instance using available AWS tools.
- Deploy sensitive components in such a manner that they are available through multiple availability zones. Also, replicate the data periodically so that data can be recovered in case of application crashing.
- Watch and respond to the events
- Prepare a strategy to handle failure. You can attach a network interface for replacement instances.
- Test your recovery process for instances and Amazon EBS volumes.
4. Use of trusted Advisor
A trusted advisor provides 4 services that help in saving money, improving system performances, reliability, and closing security gaps. These services are:
- Service Limit check
- Security Groups – Port and IP check
- Internet and Access management use check
- Multifactor Authentication on the root account.
To check the current status of the above four services, click on the trusted advisor icon on the AWS console under Administration & Security. It is one of the easiest best practices for implementation.
5. Understanding AWS shared responsibility model
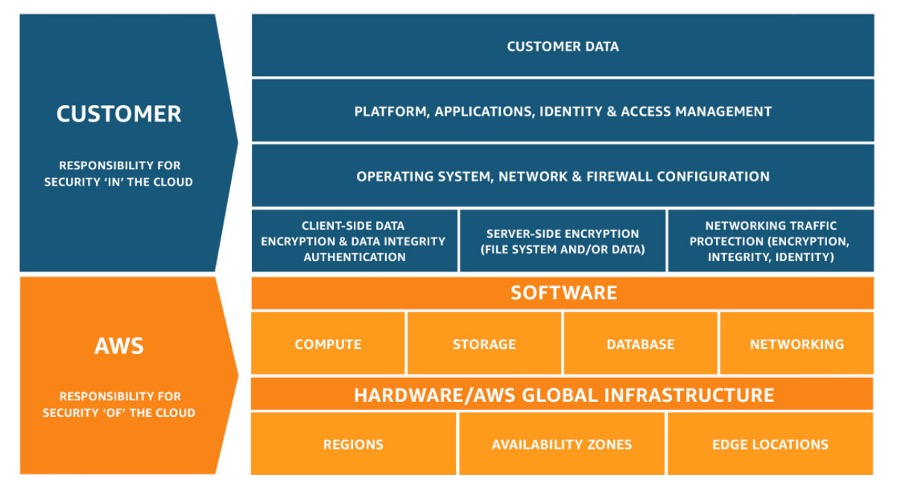
AWS believes security is a shared responsibility between AWS and the Customer. It segregates the responsibilities of the customer and AWS. Awareness of this business model helps the user in taking necessary steps that help to improve upon security and compliance.
The customer is responsible for instance configuration, firewall, and management tasks. Server-side & client-side encryption, data integrity authentication, & network traffic protection are other duties of the customer.
Also, make sure that you apply security to all layers. Build a virtual firewall to control and monitor network traffic to secure your infrastructure.
6. Configure password policy & use password generator
A strong password policy is a must for the security of the organization. Password cracking, brute force attacks are some of the most common security attacks. Creating a password policy determines password creation, modification, and deletion rules.
Apart from the password policy, password generators must be used to generate a complex secure password. It helps you in creating a relatively complex password.
Conclusion
Before setting up AWS infrastructure for your organisation, one should be thorough with the best practices of AWS. Implementing best practices will consume time but it is a proactive step that will help in mitigating issues and attacks. This article speaks of some of the best practices one can implement. Let us know through comments what best practices you have applied in your AWS.
Share your thoughts on this and AWS requirements (if any) with us at contact.us@virtuetechinc.com and we will reach out to you to help your business in the best possible manner.




